Hashing functions in SQL Server work as cryptographic instruments to produce distinct fixed-size hash values from input data. This compilation features a variety of hash algorithms, all of which are intended to provide unique hash values for a given input string.
- Once-commonly used MD2, MD4, and MD5 algorithms produce hashes with a length of 128 bits. But now since they have flaws, they are considered insecure.
- SHA1 and SHA (Secure Hash Algorithm): These algorithms, which are members of the SHA family, generate hash values with different bit lengths. Even while SHA-1 was once in use, its flaws have made it obsolete in favor of safer substitutes.
- SHA2_256 and SHA2_512: These members of the SHA-2 family provide hash values of 256 and 512 bits, respectively, and are presently regarded as secure in the context of cryptography.
1. Message Digest Algorithm 2, or MD2
A cryptographic hash function called MD2 generates a hash value of 128 bits. Although this older method is renowned for being straightforward, it has flaws and is no longer advised for use in situations where security is a concern.
As an illustration
SELECT HASHBYTES('MD2', 'Hello, World!') AS [MD2 HashValue];
2. MD4 (Message Digest Algorithm 4)
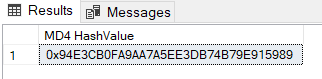
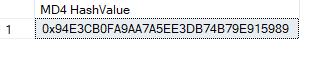
MD4 is a cryptographic hash function designed to produce a 128-bit hash value. It's also considered obsolete and insecure due to vulnerabilities.
Example:
SELECT HASHBYTES('MD4', 'Hello, World!') AS [MD4 HashValue];
3. Message Digest Algorithm 5, or MD5
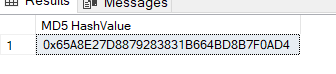
A popular cryptographic hash algorithm that produces a 128-bit hash result is MD5. However, it is no longer regarded as secure for essential applications because of weaknesses and collision attacks.
As an illustration
SELECT HASHBYTES('MD5', 'Hello, World!') AS [MD5 HashValue];
4. SHA (Secure Hash Algorithm)
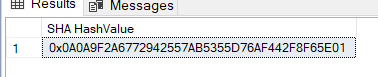
The SHA family of cryptographic hash algorithms consists of SHA-1, SHA-2, SHA-3, and SHA-0 (deprecated). More secure versions of SHA-0 and SHA-1 are gradually replacing the deemed weaker ones.
Example
SELECT HASHBYTES('SHA', 'Hello, World!') AS [SHA HashValue];
5. SHA1 (Secure Hash Algorithm 1)
A 160-bit hash value is generated by SHA-1. Although it was widely used, vulnerabilities have caused it to be deprecated. Collision attacks were successful because of its flaws.
Example:
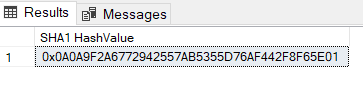
SELECT HASHBYTES('SHA1', 'Hello, World!') AS [SHA1 HashValue];
6. SHA2_256 (Secure Hash Algorithm 2 - 256 bit):
SHA-256 is part of the SHA-2 family and generates a 256-bit hash value. It's currently considered secure and widely used for various cryptographic applications.
Example
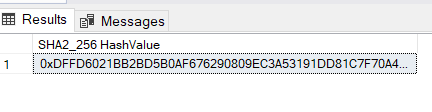
SELECT HASHBYTES('SHA2_256', 'Hello, World!') AS [SHA2_256 HashValue];
7. SHA2_512 (Secure Hash Algorithm 2 - 512 bit)
SHA-512, another member of the SHA-2 family, produces a 512-bit hash value. It's a more secure and larger variant of SHA-256.
Example
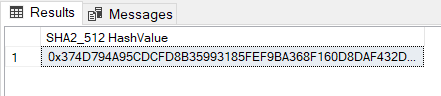
SELECT HASHBYTES('SHA2_512', 'Hello, World!') AS [SHA2_512 HashValue];
A variety of hash algorithms are available in SQL Server, and each one creates distinct hash values from input strings. Although SHA-1 and MD5 were once widely used, their flaws now warn against using them. As a safe substitute, the SHA-2 family, which includes SHA2_256 and SHA2_512, is used instead.
Selecting an algorithm that strikes a balance between security requirements and performance is crucial. Database professionals can strengthen security protocols and data integrity in SQL Server configurations by understanding these hashing subtleties.
HostForLIFE.eu SQL Server 2022 Hosting
HostForLIFE.eu is European Windows Hosting Provider which focuses on Windows Platform only. We deliver on-demand hosting solutions including Shared hosting, Reseller Hosting, Cloud Hosting, Dedicated Servers, and IT as a Service for companies of all sizes.
